BestCrypt Volume Encryption 3.50.13 | 6.21 MB
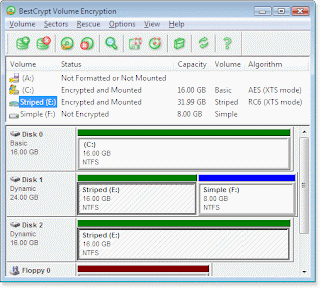
BestCrypt Volume Encryption – This is the first program that opens a new class of product that encrypts disk volumes (Disk Volume Encryption). With this software users can encrypt the disk partitions as usual, and modern disk volumes located on different disks, such as overlapping of volumes (Spanned volumes), Striped (Striped), Mirror (Mirrored) and RAID-5 volume.
BestCrypt Volume Encryption is easy to install and easy to use. With BestCrypt Volume Encryption can encrypt volumes of users and access them without keeping in mind all the information about their location on disk.
New features in version 3:
Better protection for encrypted volumes when reconfiguring disk drives.
In earlier versions the user to change the size of the encrypted volumes, as well as the location and type of the array software (Software RAID), was required to decipher them. Version 3 software automatically adapts its internal information about encrypted volumes to changes in their configuration.
Two-level authentication using conventional removable drives (eg, USB-flash drives). In the three versions of the program the user can move the encryption keys to removable media. In this case, the user who needs access to the encrypted, you must: 1) know the password of the key, and 2) have a removable media, which holds the key.
Boot the computer with the encrypted boot / system disk volume on the network. In this case, the encryption key is not stored on your computer and the remote server. This provides an additional level of security for the enterprise program. Since the keys are stored on a corporate server, access to the encrypted computer is possible only if it is connected to the corporate network.
Support for the new extended instruction set of instructions (AES-NI) for the latest Intel processors. As a result, the speed of AES encryption using AES-NI instructions increases by 5 times. The total increase in the rate of access to the encrypted disk partitions – up to 30.
The minimum initial encryption. In earlier versions the user had to encrypt the entire disk volume before using it. If the disk is large (several terabytes), the primary encryption process will take many hours. In the three versions of BestCrypt Volume Encryption, if the drive is empty, the user can start the Format. The minimum initial encryption., Thus avoiding the lengthy process of sector-based encryption. Tom is just marked as “encrypted” and all information will be recorded on the disc later, will also be encrypted. Unused disk space will remain encrypted. If desired, the user can start the process Erase. Format. The minimum initial encryption .. In this case, that will be overwritten, formatted and marked for encryption.
Automatically mount at boot time. 3 version of the device uses Trusted Platform Module (TPM), available on many motherboards to automatically reboot computer with an encrypted boot / system disk. This function is needed to manage servers that need to work around the clock. If that server is encrypted with a boot / system volume, after every reboot the server requires manual entry of a password. With this option, the server administrator can choose the time interval in which BestCrypt Volume Encryption will support automatic restart of the computer with TPM.
Device support eToken Pro Java company SafeNet (formerly Aladdin). Earlier versions of the two-tier authentication BCVE supported by a device eToken R2 and eToken Pro. eToken Pro Java – the last device, developed by SafeNet for similar purposes.
Options for connected encrypted removable drives: protection against accidental formatting and automount. If Windows detects and nezamontirovanny encrypted disk, then asks the user to format it. As a result, very often encrypted disk is incorrectly formatted. In the three versions have the option to disable these Windows messages and, if enabled by appropriate additional option, it is proposed to access the disk left asymmetric.
In the three versions of supported devices with physical sector size other than 512 bytes.
















0 comments:
Post a Comment